In order to emphasize the ability to control an application when online key validation is being used, I have created a poster. Serial Key Manager be found here.
Archives for Encryption
A possible change for machine code
In the recent issue, it was reported that machine codes are repeated approximately once per 50 different machines in SKGL 2.0.5.3. The reasons under investigation are:
- small hash value allows even more collisions.
- the machine information that is being hashed does not collect all hardware that can be changed.
The first reason is currently in focus, and I have tried to develop a piece of code that now increases the length of the machine code. It would be great if those of you who are able to test this on several machines could do so, and comment(either directly below this thread or here) how frequent the collisions are on different machines! Thank you in advance! 🙂
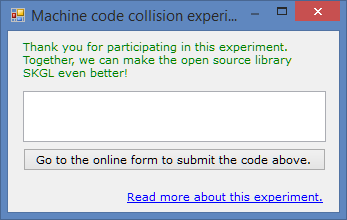
EDIT 2: This can be done by anyone using Windows:
- Download the software below (no installation required): (or download the exe file directly here) NOTE: In Google Chrome, it might tell that the file is dangerous because it is not commonly downloaded. Please right click and press keep.
- When you launch the software, you will see a 6 digit code in the text box. Please submit it here: https://docs.google.com/forms/d/1aWPKxb9Ejm_QzMciqNvFzPeJVFrNgRxaTHfM4ROUqnc/viewform.
- Thank you for your contribution! 🙂
EDIT: You can also write the machine code you get on your own computer and post it below this thread. (hardware info using dxdiag would be awesome, but the machine code is more important at this point)
public class AnalysisOfMachineCode
{
[TestMethod]
public void test()
{
Debug.WriteLine(getMachineCode());
}
[SecuritySafeCritical]
public static int getMachineCode()
{
ManagementObjectSearcher searcher = new ManagementObjectSearcher("select * from Win32_Processor");
string collectedInfo = "";
// here we will put the informa
foreach (ManagementObject share in searcher.Get())
{
// first of all, the processorid
collectedInfo += share.GetPropertyValue("ProcessorId");
}
searcher.Query = new ObjectQuery("select * from Win32_BIOS");
foreach (ManagementObject share in searcher.Get())
{
//then, the serial number of BIOS
collectedInfo += share.GetPropertyValue("SerialNumber");
}
searcher.Query = new ObjectQuery("select * from Win32_BaseBoard");
foreach (ManagementObject share in searcher.Get())
{
//finally, the serial number of motherboard
collectedInfo += share.GetPropertyValue("SerialNumber");
}
// patch luca bernardini
if (string.IsNullOrEmpty(collectedInfo) | collectedInfo == "00" | collectedInfo.Length <= 3)
{
collectedInfo += getHddSerialNumber();
}
return getEightByteHash(collectedInfo, 1000000);
}
[SecuritySafeCritical]
public static string getHddSerialNumber()
{
// --- Win32 Disk
ManagementObjectSearcher searcher = new ManagementObjectSearcher("\\root\\cimv2", "select * from Win32_DiskPartition WHERE BootPartition=True");
uint diskIndex = 999;
foreach (ManagementObject partition in searcher.Get())
{
diskIndex = Convert.ToUInt32(partition.GetPropertyValue("Index"));
break; // TODO: might not be correct. Was : Exit For
}
// I haven't found the bootable partition. Fail.
if (diskIndex == 999)
return string.Empty;
// --- Win32 Disk Drive
searcher = new ManagementObjectSearcher("SELECT * FROM Win32_DiskDrive where Index = " + diskIndex.ToString());
string deviceName = "";
foreach (ManagementObject wmi_HD in searcher.Get())
{
deviceName = wmi_HD.GetPropertyValue("Name").ToString();
break; // TODO: might not be correct. Was : Exit For
}
// I haven't found the disk drive. Fail
if (string.IsNullOrEmpty(deviceName.Trim()))
return string.Empty;
// -- Some problems in query parsing with backslash. Using like operator
if (deviceName.StartsWith("\\\\.\\"))
{
deviceName = deviceName.Replace("\\\\.\\", "%");
}
// --- Physical Media
searcher = new ManagementObjectSearcher("SELECT * FROM Win32_PhysicalMedia WHERE Tag like '" + deviceName + "'");
string serial = string.Empty;
foreach (ManagementObject wmi_HD in searcher.Get())
{
serial = wmi_HD.GetPropertyValue("SerialNumber").ToString();
break; // TODO: might not be correct. Was : Exit For
}
return serial;
}
public static int getEightByteHash(string s, int MUST_BE_LESS_THAN = 1000000000)
{
//This function generates a eight byte hash
//The length of the result might be changed to any length
//just set the amount of zeroes in MUST_BE_LESS_THAN
//to any length you want
uint hash = 0;
foreach (byte b in System.Text.Encoding.Unicode.GetBytes(s))
{
hash += b;
hash += (hash << 10);
hash ^= (hash >> 6);
}
hash += (hash << 3);
hash ^= (hash >> 11);
hash += (hash << 15);
int result = (int)(hash % MUST_BE_LESS_THAN);
int check = MUST_BE_LESS_THAN / result;
if (check > 1)
{
result *= check;
}
return result;
}
}
Two new videos about Serial Key Manager
This week I was able to record two new videos that describe the process of external validation of a license key using Serial Key Manager. Now, my final aim is to record a third, last video about the way the local time can be synced with a server to prevent user from gaining more days than allowed by a license.
Below are the videos:
An article about Licensing systems
This is an article about three different licensing systems, using C#.NET environment.
Title: Three different algorithms for constructing licensing systems, their advantages and disadvantages using C# .NET environment.
Abstract: A key validation algorithm is one of the important parts in the protection of a computer application. Even if an already existing API is to be used, it is important to understand its weaknesses in order to compare it with alternative ones. Therefore, in this article, three different categories will be described with clear definitions that will make it possible to distinguish between them and allow an analysis of currently existing APIs. Every category is accompanied with examples and in some cases suggestions for further development. The categories described in this article are Checksum based key validation, Pattern based key validation, and Information based key validation. It is going to be found that the choice of a key validation system depends on the information that is to be stored in the key. It is also concluded that at this point it would be better to use online key validation instead.
Vigenère cipher, programming contest
Yesterday I was solving an interesting question that has been used on the Swedish Computer Science contest – a programming contest, in 2010, which probably is simple, but interesting because it emphasises sequences, et cetera.
The question introduced the Vigenére cipher in a classical way, with two disks containing letters of the English alphabet. In the beginning, we know several things about the encrypted text, which are to help us when we are going to crack the message.

- The disks might have different number configurations, i.e. there is still a shift, which is unknown.
- In order to “make it harder” for the enemy, each time we have obtained a letter, we continue by using a new shift, and this shift is increased by a constant value.
- Fortunately, we get to know that each message contains the word “HEJ” – a Swedish word for “hello”, which might be used as “bye”, I think.
Also, we get some examples as well, for instance:
Example 1:
Encrypted text: LRIJOUZRIYAQIRAG
Message: HEJVITARENFIKANU – means let’s take a “fika”
Example 2:
Encrypted text: GCGDJJI
Message: HEJHOPP – hello in an optimistic manner
There is also an example of this sequence,in Example 1, which is tells us that the difference is 9, 12, 15, 18… (common difference 3).
I’m solving this using a recurrence, and I’m not simplifying this arithmetic progression in any way, I just add d all the time.
The code below has passed all their tests, which are located at the end of this post.
static void Main(string[] args)
{
/*
* Copyright (C) 2013 Artem Los,
* All rights reserved.
*
* This code-snippet can be found at:
* http://clizware.net/
*/
string alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZ";
Console.Write("Enter the message: ");
string message = Console.ReadLine();
int H = alphabet.IndexOf("H");
int E = alphabet.IndexOf("E");
int J = alphabet.IndexOf("J");
int dA = mod(alphabet.IndexOf(message[0]) - H, alphabet.Length);
int dB = mod(alphabet.IndexOf(message[1]) - E, alphabet.Length);
int dC = mod(alphabet.IndexOf(message[2]) - J, alphabet.Length);
int init1 = dB - dA;
int init2 = dC - dB;
int dConst = init2 - init1;
int dPrev = dC;
Console.Write("Output message: HEJ");
for (int i = 3; i < message.Length; i++)
{
init2 += dConst;
dPrev = mod(dPrev + init2, alphabet.Length);
int X = alphabet.IndexOf(message[i]);
Console.Write(alphabet[mod(X - dPrev, alphabet.Length)]);
}
Console.ReadLine();
}
static int mod(int n, int b)
{
return n - b * (int)Math.Floor((double)n / b);
}
}
Example 1
RIPIWDUXRS
HEJSOVERNI
Example 2
IGNUFAKPXYVSF
HEJNUKOMMERDE
Example 3
PAJESQBIPOOPKAP
HEJKOMHITGENAST
Reference:
http://www.progolymp.se/Oldpage/arkiv/kval10.pdf
http://www.progolymp.se/Oldpage/arkiv/kvalsvar10.pdf
A new feature is coming to SKGL Project
In order to decrease the distribution of serial keys over ‘bad’ hacking sites, I would like to present a feature that probably will be released in SKGL 2.1.1.0 – Machine code locking. This means that each serial key will have support for machine code storage, so that the serial key is bounded to a single computer. As you know, the project is open source, and you can join it whenever you want to (http://skgl.codeplex.com/). If you think I should change something, please write to me or comment this post. Good Luck!
static string getMachineCode()
{
/*
* Copyright (C) 2012 Artem Los, All rights reserved.
*
* This code will generate a 5 digits long key, finger print, of the system
* where this method is being executed. However, that might be changed in the
* hash function "GetStableHash", by changing the amount of zeroes in
* MUST_BE_LESS_OR_EQUAL_TO to the one you want to have. Ex 1000 will return
* 3 digits long hash.
*
* Please note, that you might also adjust the order of these, but remember to
* keep them there because as it is stated at
* (http://www.codeproject.com/Articles/17973/How-To-Get-Hardware-Information-CPU-ID-MainBoard-I)
* the processorID might be the same at some machines, which will generate same
* hashes for several machines.
*
* The function will probably be implemented into SKGL Project at http://skgl.codeplex.com/
* and Software Protector at http://softwareprotector.codeplex.com/, so I
* release this code under the same terms and conditions as stated here:
* http://skgl.codeplex.com/license
*
* Any questions, please contact me at
* * artem@artemlos.net
*/
ManagementObjectSearcher searcher = new ManagementObjectSearcher("select * from Win32_Processor");
string collectedInfo = ""; // here we will put the informa
foreach (ManagementObject share in searcher.Get())
{
// first of all, the processorid
collectedInfo += share.GetPropertyValue("ProcessorId").ToString ();
}
searcher.Query = new ObjectQuery("select * from Win32_BIOS");
foreach (ManagementObject share in searcher.Get())
{
//then, the serial number of BIOS
collectedInfo +=share.GetPropertyValue("SerialNumber").ToString ();
}
searcher.Query = new ObjectQuery("select * from Win32_BaseBoard");
foreach (ManagementObject share in searcher.Get())
{
//finally, the serial number of motherboard
collectedInfo+= share.GetPropertyValue("SerialNumber").ToString();
}
return GetStableHash(collectedInfo ).ToString ();
}
static public int GetStableHash(string s)
{
/*
* modification of code from:
* http://stackoverflow.com/questions/548158/fixed-length-numeric-hash-code-from-variable-length-string-in-c-sharp
*
* modified by Artem Los
*
*/
const int MUST_BE_LESS_OR_EQUAL_TO = 100000;
uint hash = 0;
foreach (byte b in System.Text.Encoding.Unicode.GetBytes(s))
{
hash += b;
hash += (hash << 10);
hash ^= (hash >> 6);
}
hash += (hash << 3);
hash ^= (hash >> 11);
hash += (hash << 15);
int result = (int)(hash % MUST_BE_LESS_OR_EQUAL_TO);
int check = MUST_BE_LESS_OR_EQUAL_TO / result;
if (check > 1)
{
result *= check;
}
return result;
}
Get Hash Code with Java Script
Once, I wrote about hash function that I improved. Though, that was C#. In this post I will show you how to get hash code with Java Script. (previous post)
function getStableHash(input,hashLength)
{
/* Copyright (C) 2012 Artem Los,
* All rights reserved.
*
* code based on:
* http://blog.clizware.net/news/631
*
* originaly from: http://stackoverflow.com/questions/548158/fixed-length-numeric-hash-code-from-variable-length-string-in-c-sharp
*/
var _length = Math.pow(10,hashLength); //result in 10 numbers, if hashLength is 10
var hash = 0;
for (var j = 0; j < input.length; j++)
{
hash += input.charCodeAt(j);
hash += (hash << 10);
hash ^= (hash >> 6);
}
hash += (hash << 3);
hash ^= (hash >> 11);
hash += (hash << 15);
var result = ((hash % _length) + _length) % _length;//hash.mod(_length)
var check = parseInt(_length / result);
if (check > 1)
{
result *= check;
}
return result;
}
In order to calculate a hash value, you need to define two main variables. First of all, the string to calculate hash from (input), and eventually, the length of the result (hashLength). It is recommended that you set the hashLength to 8 or in some cases 10.
Please take a look at this code in work http://editor.clizware.net/?id=9
Hash code generator
Dear Readers,
The last time I have spent on the development of SKGL API, which is a library for those of you who want to secure, protect your hard-coded .NET application. I meanwhile, I have also spent sometime on a code, (basically half an hour), that produces hash code. It is not the best way of doing it, however, so it would be a pleasure to see another version of this code. Much appreciated!
static string twentyfiveByteHash (string s)
{
int amountOfBlocks = s.Length / 5;
string[] preHash = new string[amountOfBlocks];
if (s.Length <= 5)
{
//if the input string is shorter than 5, no need of blocks!
preHash[0] = GetStableHash(s).ToString ();
}
else if (s.Length > 5)
{
//if the input is more than 5, there is a need of dividing it into blocks.
for (int i = 0; i < amountOfBlocks-1; i++)
{
preHash[i] = GetStableHash (s.Substring(i*5,5)).ToString ();
}
preHash[preHash.Length-1] = GetStableHash (s.Substring((preHash.Length-1) * 5, s.Length - (preHash.Length - 1) * 5)).ToString ();
}
return String.Join ("",preHash);
}
static public int GetStableHash(string s)
{
/*
* modification of code from:
* http://stackoverflow.com/questions/548158/fixed-length-numeric-hash-code-from-variable-length-string-in-c-sharp
*
* modified by Artem Los
*
*/
const int MUST_BE_LESS_OR_EQUAL_TO = 100000000;
uint hash = 0;
foreach (byte b in System.Text.Encoding.Unicode.GetBytes(s))
{
hash += b;
hash += (hash << 10);
hash ^= (hash >> 6);
}
hash += (hash << 3);
hash ^= (hash >> 11);
hash += (hash << 15);
int result = (int)(hash % MUST_BE_LESS_OR_EQUAL_TO);
int check = MUST_BE_LESS_OR_EQUAL_TO / result;
if (check > 1)
{
result *= check;
}
return result;
}
Tip of this weekend (25/2-12)
Another good method to encrypt ASCII based text. To view this example in work, http://editor.clizware.net/?id=7 (remember to press compile)
//Copyright (C) 2012 Artem Los, All rights reserved
function mod_c(text,key,enc_dec)
{
//only for 128 ascii values
if (key == "")
{
return "Error: no key given";
}
if (enc_dec === true)
{
var result = "";
for (var i=0; i < text.length; i++)
{
result += String.fromCharCode( (text.charCodeAt(i) + key.charCodeAt(i % key.length)).mod(128) );
}
return result;
}
else if(enc_dec === false)
{
var result = "";
for (var i=0; i < text.length; i++)
{
result += String.fromCharCode( (text.charCodeAt(i) - key.charCodeAt(i % key.length)).mod(128) );
}
return result;
}
else
{
return "Error: enc_dec is not given";
}
}
Number.prototype.mod = function(n) {
return ((this%n)+n)%n;
}
Encrypting a website
EDIT: Please check out the updated version of this article.
When encrypting a website, we need to understand the way a browser interprets our input, i.e. html/javascript. In this case, we can produce code that is only readable by a browser.
There are several ways to encrypt a page, the main idea behind all methods is it to convert a human-readable code to ONLY computer-readable one.
- By HTML only
- By JavaScript
- Using hexadecimal values
- Using “escape/unescape”
- Using an advanced algarithm
By HTML Only
In HTML, all letters(chars) can be written in a ASCII form, i.e., if we have a small “a” that is to be converted, we simply look up its ASCII value and write it instead of the actual char: a, and so on.To sum up, the prefix is “&#”, then the ASCII code, and lastly a semicolon, “;”.
function encToASCII(_text)
{
var _newText="";
for(var i=0; i < _text.length;i++)
{
_newText += "&#" + _text.charCodeAt(i) + ";";
}
return _newText;
}
By JavaScript
JavaScript website encryption can be divided into several parts. One way is by using the hexadecimal value of a char, and write it instead of the actual char. We have to use JavaScript to perform this action, as it is shown below:
function encToHex(_text)
{
var _newText="";
for (var i=0; i < _text.length; i++)
{
_newText += "%" + decimalToHex(_text.charCodeAt(i));
}
return _newText;
}
function decimalToHex(_num)
{
return _num.toString(16);
}
This method will only encrypt the given text, though, but, the user has to be able to see the encrypted text as a result (the browser won’t understand this code unless we have a function that will interpret it). This method is based on JavaScript, and we therefore need to use JavaScript to decrypt. Let us say that we encrypt “Hello World!”, which results “%48%65%6c%6c%6f%20%57%6f%72%6c%64%21”. As you might see, the prefix is “%”, and then the hexadecimal number. If the result above is our webpage, the source of that webpage should look similar to the example below:
<script type="text/javascript">
document.write(unescape("%48%65%6c%6c%6f%20%57%6f%72%6c%64%21"));
</script>
There is also, as you might see, an opportunity to use functions escape and unescape as they are. Their actual usage is to encode/decode the url, i.e., replacing spaces, “special chars.” to url friendly one. All letters and numbers will stay the same, they will not be changed.
document.write(escape("Hello World!"));
The result you will get is Hello%20World%21. It replaces spaces with %20, and “!” with %21. Both of them are special characters(chars).
Unescape function will decode to a normal string.
document.write(unescape("Hello%20World%21"));
It took a while for me to define what an advanced algorithm in our case would be. I would say that the more advanced algorithm you have, the more time it takes to “crack it”. The method that will be described in this section of the post is my own little version of advanced algorithm. The method is using a logical operation, called XOR. If you already now what that is, jump to the next section.XOR is an operator, and works at a binary level. A definition in words is that the first or second value is true, but not both. Truth table shown below:
| Input | Output | |
|---|---|---|
| A | B | |
| 0 | 0 | 0 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 1 | 1 | 0 |
| XOR Truth table | ||
An operation, 5 XOR 6, would result 3. The thing is, if we take either 5 XOR 3 = 6 or 6 XOR 3 = 5, we always return to our previous numbers. Conclusion, if two numbers are known, we always will get the third one.
| 1 | 0 | 1 |
| 1 | 1 | 0 |
| 1 | 1 | 0 |
By using XOR operation, we might, for instance, set a secret number, or a series of numbers, which always will return our third number. In this post, we will go though how to use a series of numbers, but also how to do it with only one number.
function en_doc(t,k)
{
var a;
var b;
var r=new Array();
for (var i=0; i<t.length ;i++)
{
a=t.charCodeAt(i);
b=k.charAt(i%k.length);
a^=b;
r[i]=String.fromCharCode(a);
}
return r.join("");
}
The code shown above is my own advanced algorithm. First, we declare “a”, which is a char at certain place in string t; and b, which is a digit at certain place in k. The text to encrypt is placed in t (all chars), and the key to encrypt with is placed in k (only digits). The variable r is an array of the result/output.
First of all, we assign a to the char code at i. The variable b is then assigned to the char at i mod the length of key.
The reason why I put a modular operation there is simple. If the key length we use is smaller than the text length, we will not be able to encrypt the whole string without it. When we are encrypting something, the key has to be of the same length as the text. By using a modular operation, even if the key is smaller than the text, it will be repeated. For example, if the key is 567 (key length=3), and the text length is 6, the output key will result 567567.
Secondly, an logical operation is executed. In other words, variable a equals to itself XOR b. Variable a has therefore a new value which is later assigned to r[i], i.e., a place in the array r which corresponds to the index value i.
Lastly, we join our array without some joining char, and that will be our encoded text. To decrypt, use the same function; place your encrypted text in t, and the key in k.
You can, however, remove this key opportunity, or as I previously defined it, using a key series, to a single key digit. You might still use this method, but only having a key, for instance, 6, or, you might remove it at all, and set the secret digit inside the function.
If you want to include this code in your project without typing the code above, include this code before all scripts (see this code in action):
Source 1:
<script src="https://dev.clizware.net/lib/scrypto1.js"></script>
Source 2:
<script src="https://clizware.webs.com/lib/scrypto1.js"></script>
I hope this article was useful, and that you hopefully have learned something new! Below you find some useful links:
Encrypter – (for html only encryption)
http://www.iwebtool.com/html_encrypter – (encrypting to hexadecimal values, javascript)
Bitwise Operators – (about logical operators)
Escape and Unescape
Eval – (advanced encryption, etc.)
This article was revised 17.03.2013.